“Deadbolt” ransomware attacks on QNAP devices

Launched in January, 2022, the new DeadBolt ransomware targets QNAP devices by encrypting the files contained on the device, adding the “.deadbolt” extension to their names.The ransomware also grabs the QNAP login screen to display a ransom note demanding 0.03 BTC (see the picture below).
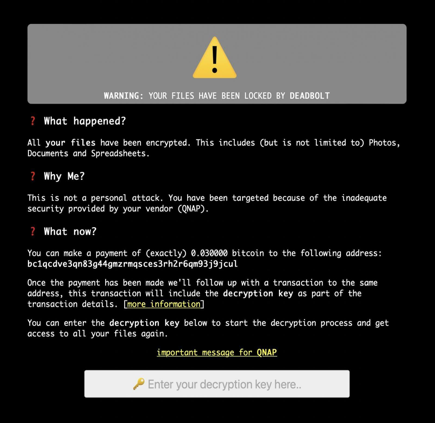
Each victim receives a unique bitcoin wallet address to transfer the ransom. After the specified transaction is completed, the second transaction’s hash arrives at the extortionist’s unique address and serves as a decryption key for the attacked files on the QNAP devices.
The TokenScope team analyzed the bitcoin wallet addresses owned by the ransomware to determine withdrawal path and to identify “cold wallets” where fraudulently obtained funds could possibly be stored.
Thus, the analysis of one of the addresses indicated by the ransomware bc1qg0trvemr4ldsfrmzz9ulc283y26w9f37pvge89 made it possible to reveal that the address was created on February 2, 2022, with 2 incoming transactions carried out on the same day. Not a single outgoing transaction was carried out, current balance is 0.0300546 BTC.
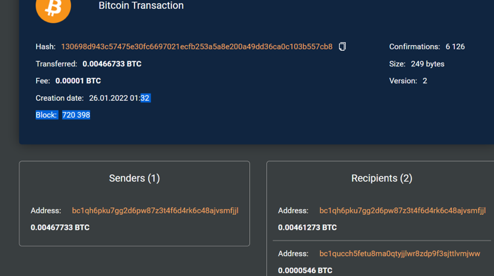
In addition to the ransom payment (replenishment by 0.3 BTC), the extortionist’s address was also replenished on February 2, 2022 at 18:17 by the amount of 0.0000546 BTC from the address bc1qh6pku7gg2d6pw87z3t4f6d4rk6c48ajvsmfjjl (the address was created on January 21, 2022, the last transaction of the address was on March 15, 2022, the address turnover is 0.29 BTC, current balance is 0.29 BTC).
The address has been replenished by 231 transactions, with 10 transactions in the amount of 0.001 BTC, the rest transactions are for smaller amounts. The analysis of incoming transactions of the wallet revealed that it was replenished, among others from bc1qm34lsc65zpw79lxes69zkqmk6ee3ewf0j77s3h wallet, the address is on the Binance exchange and it is mentioned on Twitter as a wallet that sold 3900 BTC in a day DEBJIT HIRA (@HiraDebjit) / Twitter.com.
The analysis of outgoing transactions of the address bc1qh6pku7gg2d6pw87z3t4f6d4rk6c48ajvsmfjjl allowed the TokenScope analysts to identify the following pattern: in most cases, the transferred funds have been returned to the remitter’s address, while the change in the amount of 0.0000546 BTC is transferred to another address, the same to witch the ransom in the amount of 0.03 BTC was paid.
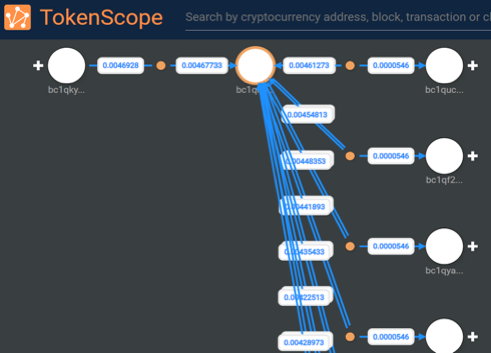
Following this logic, the TokenScope investigation identified 292 addresses, on each the amount of 0.03 BTC has been received, highly likely, all these addresses are related to one and the same extortion, perhaps belonging to one person or a group of persons. The funds have not yet been withdrawn, each of them has balance 0.0300546 BTC generated by 2 transactions, without any outgoing transactions:
- bc1qucch5fetu8ma0qtyjjlwr8zdp9f3sjttlvmjww
- bc1qf2ytuua8sc8dkjqyx79nzj7nk6xgqaqxcwxmwk
- bc1qya4auwfllzs4z598rsa0y5k2eze7dv2rr0fden
- bc1qnkadhgtn9qw08xwxer49g88s3q673ck0x7xwy0
- bc1qp0qxsa90a9k35lvfeg7dmcpc3llz0farfxkfua
- bc1qmcv74psf0mpkfasrl7aqwrk584x0ews6zl4zw3
- bc1qv9fv5w3z57rf3dyr06r7lxs5zkvgnt75n563kf
- bc1qrru3murzyp2dy065y8q638rpdh0xf6vy2trzdd
Thus, the total amount of funds collected by extortionists is 8.7 BTC, which is more than $354 000 at the current exchange rate.




