Deadbolt ransomware collects over $1M

TokenScope experts continue to monitor and analyze attacks of the DeadBolt ransomware against QNAP devices, which we covered in a previous article, “Deadbolt” ransomware attacks on QNAP devices.
More than six months later after the previous publication, the ransomware virus is still active and extorts money almost on a daily basis, providing users a way to decrypt infected data in exchange for ransom. No effective and universal solution to decrypt data otherwise has been invented yet, but there are some positive aspects that we will cover in this review.
As we mentioned before, first DeadBolt ransomware attacks against QNAP and ASUSTOR devices were detected on January 21, 2022. The virus broke into the NAS device authentication page and displayed a message saying that the files were blocked by DeadBolt and an amount of 0.03 BTC (0.05 BTC from September) had to be paid in order to decrypt them. Once deployed onto the device, the ransomware encrypted the files on it using the AES128 algorithm and added the .deadbolt extension to their names.
Every victim receives a unique bitcoin wallet address to transfer the ransom. As soon as the transaction is completed, a second transaction goes to the ransomware’s unique address, with its hash value serving as the decryption key for the attacked files on the respective QNAP device.
In a previous review, “Deadbolt” ransomware attacks on QNAP devices, we described the ransomware scheme in detail; by that time (March 2022) it had collected 8.7 BTC from 292 addresses.
In particular, all the wallets to which the users who found their data encrypted are to transfer the ransom are unique and newly created, and only when the ransom is received by the perpetrators, these wallets generate a second transaction from the address bc1qh6pku7gg2d6pw87z3t4f6d4rk6c48ajvsmfjjl, and that second transaction contains the decryption key.
The address bc1qh6pku7gg2d6pw87z3t4f6d4rk6c48ajvsmfjjl is the central address of the DeadBolt ransomware, since it is linked to all the addresses to which the ransom is transferred. In addition, it is used as a path through which transactions with the decryption code are created in an automated mode, once the ransom is credited to the unique address. You can see a diagram of the transactions carried out via
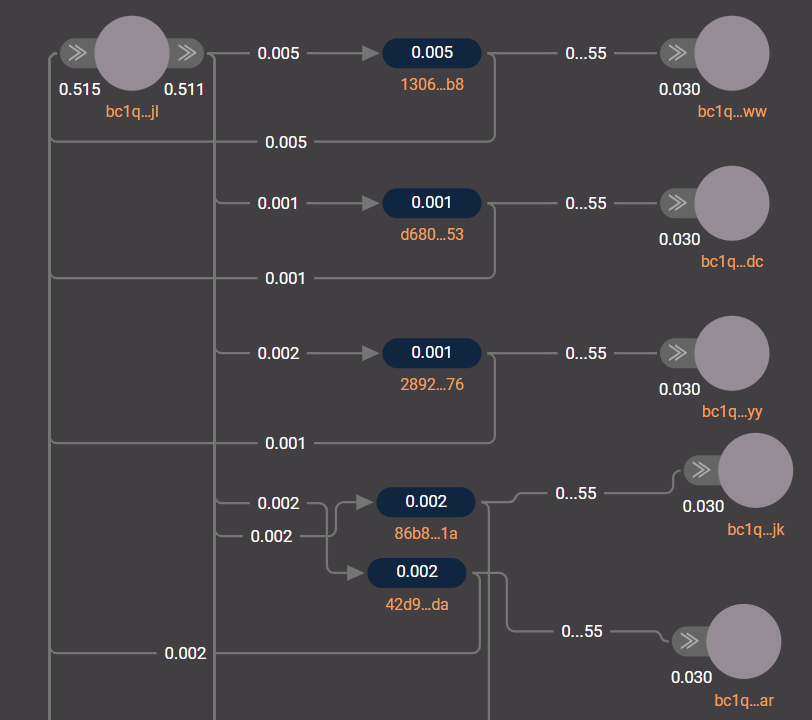 bc1qh6pku7gg2d6pw87z3t4f6d4rk6c48ajvsmfjjl at this link.
bc1qh6pku7gg2d6pw87z3t4f6d4rk6c48ajvsmfjjl at this link.
Analysis of activity at bc1qh6pku7gg2d6pw87z3t4f6d4rk6c48ajvsmfjjl makes it clear that ransom payment activity remained at about the same level from January to late April 2022, then it declined, but, afterwards, a strong surge of activity was observed in mid-May, with another fall until September of this year and another steep rise after that.
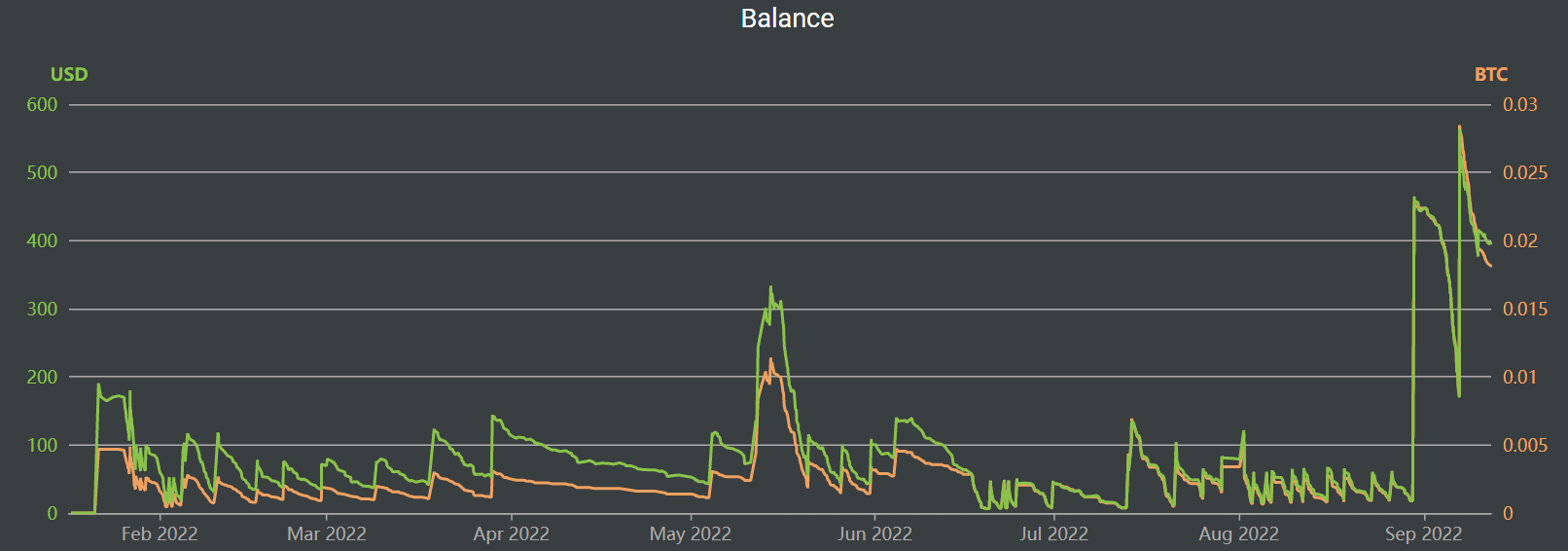
Let us try and analyze the events that could be associated with the changes in the transactional patterns at the ransomware address. By the end of April, major antivirus product providers had developed information decryption solutions, but in mid-May the perpetrators found another “breach” in the protection of QNAP devices, which resulted in the multiplication of attacks.
On May 20, 2022, QNAP, a Taiwan-based NAS manufacturer, warned its users that they should secure their devices against new DeadBolt ransomware attacks. The company recommended to update NAS software to the latest version and to disable remote access to the devices via the Internet.
In September 2022, the Norwegian police conducted a special operation against the organizers of the criminal scheme. The police tricked the extortionists into creating decryption keys, and cancelled their transactions before they were included in the block. Under to the fraudsters’ initial scheme, decryption keys were sent to the victims immediately, even before validation of the transaction. This allowed law enforcers to make fake ransom payments with low fees at a time when the blockchain was heavily overloaded. Because its took the blockchain some time to validate the transactions, the police, in turn, had time to make the transactions, receive 155 keys, and immediately cancel the payments.
As a result of the successful operation, RespondersNU, in cooperation with the Dutch police and Europol, created the website deadbolt.responders.nu, where DeadBolt victims who have not contacted the police or been identified can check to see if a key for their affected device is listed among the keys tricked from the attackers.
Unfortunately, the ransomware hackers figured out how exactly they were duped, so the ransom amount has since been increased to 0.05 BTC, and now transactions require double validation before the victims are issued the key to decrypt their data.
Statistics shows that the ransomware continues to hit NAS devices to date, and users still pay a ransom to decrypt their data. According to the Norwegian police, as of today, more than 20,000 devices have been infected worldwide.
Notably, ever since DeadBolt’s first appearance, cybercriminals have offered to disclose full information about the vulnerabilities to QNAP for 5 BTC, or sell QNAP itself a key to decrypt all infected devices for 50 BTC. A similar proposal was made to ASUSTOR, for 7.5 BTC and 50 BTC, respectively. The addresses for depositing those amounts are unique and single-use; we have not discovered any payments made to them.
As a service, TokenScope is able to monitor the addresses whose activity is of interest to the user. As a result of tracking the activity of an address belonging to the DeadBolt ransomware, bc1qh6pku7gg2d6pw87z3t4f6d4rk6c48ajvsmfjjl, it can be inferred that the ransomware had collected over 70 BTC in ransom, stored across 20,000+ addresses as of November 29, 2022, which equals nearly $1.15 million at current exchange rates, with bitcoin standing at $16,500.




